Android Phone Sniffer Tool

Jun 12, 2021 Best WhatsApp Spying App – WhatsApp Sniffer for Android is currently one of the best and most used WhatsApp spy apps around the world. The latest version of this app has many advanced features which everyone will find useful. Android MultiTool 4.0 on 32-bit and 64-bit PCs. This download is licensed as freeware for the Windows (32-bit and 64-bit) operating system on a laptop or desktop PC from mobile phone tools without restrictions. Android MultiTools 4.0 is available to all software users as a free download for Windows.
In addition to using secure protocols and encrypting information, most business concerns can prevent attacks by using packet sniffer tools software that can detect wireless network sniffers. When you are looking for one such useful software for your business, you can search for them in Google by typing packet sniffer tools Windows, list of packet sniffing tools, HTTP packet sniffer, open source packet sniffer, different packet sniffing tools, network sniffing tools, best-sniffing tools and packet sniffing programs.
Related:
WireShark Packet Sniffer
This is by far the first network protocol analyzer across the planet that allows a user to access the heavy PCap files and obtain the needful reports in a very short span. It offers a rich and seamless experience with the help of advanced alerts and triggers. It also comes with fully integrated efforts of AirPcap and Wireshark.
SmartSniff
This HTTP packet sniffer can automatically scan all the PCs that work on a specific network and then build a report with details about installed hardware & software, their OS along with other crucial alerts. You can also analyze and troubleshoot the Wi-Fi network along with monitoring the opened TCP or IP ports or other connections on your network.
Microsoft Message Analyzer
This packet sniffer tools for Windows allow its users to capture, display and analyse the protocol messaging traffic with ease. It is equipped with loads of features that proffers support for more than one message provider and is able to import text logs before they are parsed into the key element or value pairs.
The Best Packet Sniffer Tools for other Platforms
The greatest benefit of the packet sniffer Tools Post is that they are now available on separate platforms so that you can seamlessly capture and analyze the live data and retrieve the archived message sets from logs and traces. Now you can display the high-level data summaries in a default view system with the following software.
Packet Capture for Android
This open source packet sniffer for Android allows you to capture packet and network traffic sniffer with SSL decryption and it is extremely helpful for creating apps. You can capture data and record them without the need of any roots or set up a dedicated proxy server on your PC and you can work with this software just if you own an Android device.
Cocoa Packet for Mac
This packet sniffer tool for Mac users comes in several versions. It aids in allowing visibility of network in varying degrees that can be defined as per your requirements. With the passive decoding and recording of network data, you can now determine the security strength of your personal network.
Dsniff for Windows
This is one of the best network sniffing tools for Windows that allows seamless network penetration and auditing along with passively monitoring the network to find out interesting data. It can easily detect the vulnerability of any network application protocols so that you can protect it from any kind of credential theft.
Packet Peeper – Most Popular Software
This is by far the most useful packet sniffer ToolPost loaded with a wide array of features that include TCP stream reassembling, multiple capture sessions, privilege separating, and filters which can be customized anytime you want to. You can also use the python plugins and avail the support for Pcap or TCPdump capture filings. You can also see Traceroute Software
What is Packet Sniffer Tools?
Wireless packet sniffers are crucial for the maintenance of wireless networks and their features have made them very popular among malicious actors as well. Wireless sniffer software programs allow intrusion as well as hidden network detection for discovering malicious sniffers present on the networks. Besides including features that are used in wireless sniffer tools, there are various aftermarket features which are purposely devised for detecting sniffing attacks. It is also possible for detecting sniffers in the promiscuous mode by sniffing one’s own network to detect any hacking activity. You can also see Voipmonitor Software
As you can see, the packet sniffer Tool Post is the reasonable solution for capturing as well as visualizing the traffic that flows through a network. They are extremely useful in security and network troubleshooting and since most of them can be installed without incurring much cost, they are a great aid for all who are willing to present packet data.
Related Posts

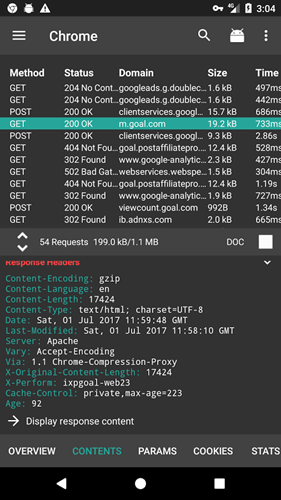
Objective: Sniff and intercept HTTP/HTTPS traffic sent from an Android device (phone or tablet) that does not have root access.
If you have a rooted Android device, you can sniff all the HTTP and HTTPS traffic using Shark for Root, a tcpdump based sniffing app. But, even with such an app, you will not be able to decode HTTPS traffic.
If you do not have a rooted Android device, and if you want to sniff HTTP/HTTPS traffic, you will need to use a MITM (man-in-the-middle) proxy that is capable of sniffing SSL traffic.
How MITM Proxy Method Works
In short, the following diagram explains the traffic flow with a MITM proxy.
The phone (P) is configured to use the MITM proxy (M) via a Wi-Fi network (AP). All HTTP/HTTPS traffic from the phone will pass through the MITM proxy. The MITM proxy will then forward the HTTP/HTTPS request from the phone to the required destination server (S). As long as the client certificates have been installed on the Android phone, the MITM proxy will be able to decrypt the HTTPS traffic sent from the Android device.
As for the response from the destination server, it will be sent to the MITM proxy. The MITM proxy will then forward this response back to the phone over the Wi-Fi network.
Network Setup
For the MITM proxy, we will be using mitmproxy. It can be installed on both Linux and Windows. For this article, I will use a Linux machine. On Debian based (Ubuntu, Kali, etc) Linux, you can install the software using the following syntax.

Android Phone Sniffer Tool Free
Once installed, start the proxy. It will listen on all interfaces on port 8080. Note that this MITM proxy (M) and the Android device (P) must reside on the same (Wi-Fi) network.
Next, enable Wi-Fi on the Android device. Then, modify the Wi-Fi settings and add the MITM proxy address. For my case, the PC (M) running mitmproxy has an IP of 192.168.10.13 and the port is 8080. My phone has an IP of 192.168.10.14. Both my Android phone and the Linux PC are on the 192.168.10.0/24 network.
Next, on your Android device, open up your browser and visit the site mitm.it. Click on the Android icon and follow the setup instructions to install the client certificate.
Now, the MITM proxy should be ready to intercept traffic from the Android device. You will now see all the HTTP/HTTPS requests from the Android device on the terminal window where the mitmproxy process was started.
Android Phone Sniffer Tool Mac
You will be able to view every individual HTTP/HTTPS request and response from the mitmproxy console. For more information on how to navigate through the mitmproxy console, refer to the documentation here.
Final Words
If you intend to sniff large amount of data, use mitmdump instead of mitmproxy.
This method will only work when the Android device is using Wi-Fi for internet access. It will not work if the Android device is using mobile data.
This method of intercepting traffic does not work with certain apps, most notably WhatsApp. From what I know, WhatsApp checks the certificates on the server before sending any traffic.
Mohamed Ibrahim
Android Phone Sniffer Tool App
ibrahim = { interested_in(unix, linux, android, open_source, reverse_engineering); coding(c, shell, php, python, java, javascript, nodejs, react); plays_on(xbox, ps4); linux_desktop_user(true); }